Webhooks
ImportantNever consume the Payment Intent related payload before validating the signature. Check the example Recipe for the code to validate the webhook signature header.
When an event related to a PaymentIntent occurs, Coinify will send an HTTP callback to your system using the HTTP POST verb.
For each Coinify environment (sandbox or production) you want to integrate with, you must set your Webhook URL and the Shared Secret on your Coinify dashboard in order to start receiving callbacks:
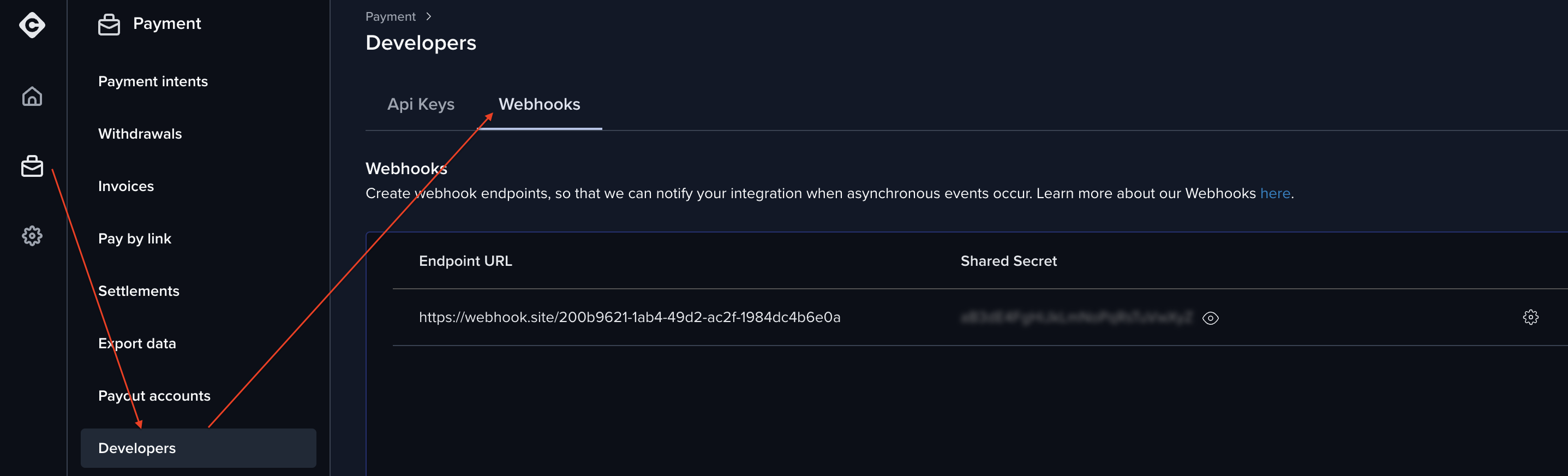
To set the webhook URL and shared secret on your dashboard, follow the link below for the respective environment you need:
Updated 5 months ago
